Page History
...
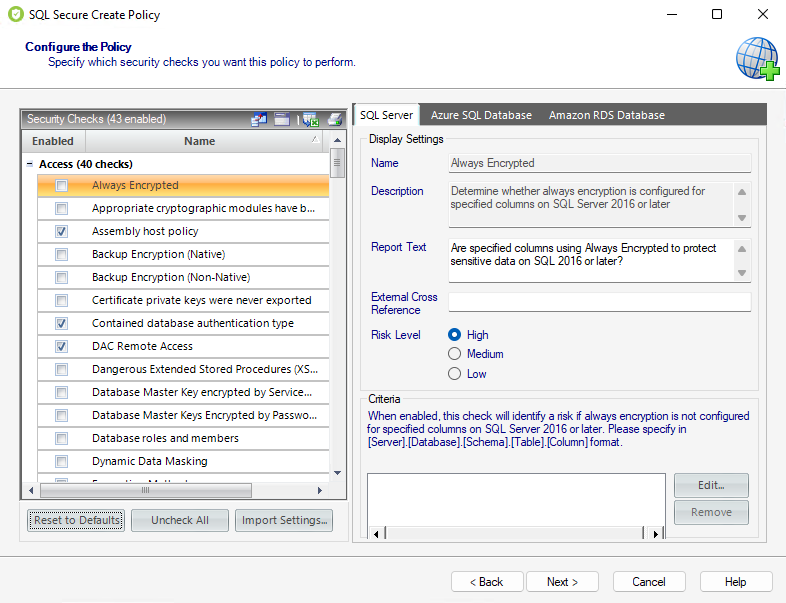
Security checks assess the vulnerability of specific Windows OS, SQL Server objects, Azure, and Amazon environments based on your criteria. Each policy has a predefined number of enabled security checks, however, the user can remove or add security checks in this section.
The list of security checks is separated by the following groups according to the type of evaluation they perform:
- Access Security Checks
- Auditing Security Checks
- Configuration Security Checks
- Data Integrity Security Checks
- Login Security Checks
- Permissions Security Checks
- Surface Area Security Checks
| Info |
|---|
Define criteria on the Security Checks that require it; otherwise, you cannot go back nor continue with the creation of a policy. |
| Note |
|---|
When security checks are set up for your policies, it is important that accurate criteria is entered. For example, a typo in the Windows Operating System Version metric criteria could cause erroneous findings. |
and SQL Server objects based on your criteria. After security checks are configured and your SQL Server instances are assigned to the policy, you can view the assessment results on the Security Summary view and on the Risk Assessment report.
In addition, you can configure email notifications to be sent out when a particular risk level has been passed. For more information, see Configure Email Notifications.
...
...
When security checks are setup for your policies, it is important that accurate criteria is entered. For example, a typo in the Windows Operating System Version metric criteria could cause erroneous findings.
Configure check settings
When you select security checks, you can configure the check settings on the right side of this window. Below the Name and Description of the respective security check you can find the following fields:
...
This field allows you to cross-reference a security vulnerability included in your report to a number or name contained in an external security standard, such as a specific HIPAA regulationHIPAA regulation.
Risk Level
This option allows you to set the severity of the risk for this security check finding. The risk level is important because it reflects how severe or risky a particular security finding is for your environment, allowing you to further customize security checks to meet your exact auditing needs. For example, finding an enabled Guest account on one instance may be a high risk, but on another instance, it may be a low risk. The risk level also determines where the corresponding security finding appears on the policy or assessment Report Card and whether or not email notifications will be sent.
...
Some security checks allow you to configure the assessment criteria, such as specific user accounts, stored procedures, or the login audit level. Text entered in this field must use the exact spelling of the object being checked. Use the option Edit and a new window opens where you can specify multiple criteria items (one per line). To delete any previous previously specified criteria, click the corresponding item, and then Remove.
...
Click Next to go to the Assign SQL Servers to the Policy section.
| Excerpt |
|---|
SQL Secure tells you who has access to what on your SQL Server databases. Learn more > > |
...