Page History
What is a Certificate?
A certificate is a public key labeled with information to identify its owner (Subject Name) and to control its use.
What is self-signed certificate?
A self-signed certificate is one for which the Issuer Name (signer) is the same as the Subject Name (owner).
What makes a certificate a CA certificate?
When it is used to issue other certificates.
It also contains information (extensions) that support its roles of issuing certificates (CRLDistPoint, BasicConstraints etc...).
It should also contain the BasicConstraints extension with the CA flag set to true.
Root or top-level CA certificates are self-signed.
What is the certificate thumbprint
The certificate thumbprint is a hash calculated on the whole certificate.
This thumbprint is calculated every time a certificate is displayed - it is not contained in the certificate.
What goes into a Certificate?
The X.509 standard defines what information can go into a certificate, and describes how to write it down (the data format).
All X.509 certificates have the following data, in addition to the signature:
Version | Identifies which version of the X.509 standard applies to this certificate. |
|---|---|
Serial Number | The entity that created the certificate is responsible for assigning it a serial number to distinguish it from other certificates it issues. This information is used in numerous ways, for example when a certificate is revoked its serial number is placed in a Certificate Revocation List (CRL). |
Signature Algorithm Identifier | The algorithm used by the CA to sign the certificate. |
Issuer Name | The name of the entity that signed the certificate. |
Validity Period | Each certificate is valid only for a limited amount of time. |
Subject Name | The name of the entity whose public key the certificate identifies. |
Subject Public Key | The public key of the entity being named, together with an algorithm identifier that specifies which public key crypto system this key belongs to and any associated key parameters. |
Versions
Version 1 has been available since 1988, is widely deployed, and is the most generic.
...
For example, if a certificate has the KeyUsage extension marked critical and set to "keyCertSign" then if this certificate is presented during SSL communication, it should be rejected, as the certificate extension indicates that the associated private key should only be used for signing certificates and not for SSL use.
Encoding Format
All the data in a certificate is encoded using two related standards called ASN.1/DER. Abstract Syntax Notation 1 describes data. The Definite Encoding Rules describe a single way to store and transfer that data.
...
The OID is a unique sequence of hierarchical numbers in a dot notation.
Top level OID assignments:
...
0 | ITU-T assigned |
1 | ISO assigned |
2 | Joint ISO/ITU-T assignment |
Secondary level assignments:
...
2.5 | X.500 Directory Services |
Other level assignments:
...
...
2.5.4
...
...
2.5.4.3
...
Common Name
...
2.5.4.5
...
Serial Number
...
2.5.4.6
...
Country Name
...
2.5.4.7
...
Locality
...
2.5.4.8
...
State
...
2.5.4.10
...
Organization
...
2.5.4.11
...
Organizational Unit
...
...
2.5.29
...
Object Identifiers for Version 3 extensions
...
2.5.29.14
...
Subject Key Identifier
...
2.5.29.15
...
Key Usage
...
2.5.29.17
...
Subject Altervative Name
...
2.5.29.19
...
Basic Constraints
...
2.5.29.35
...
Authority Key Identifier
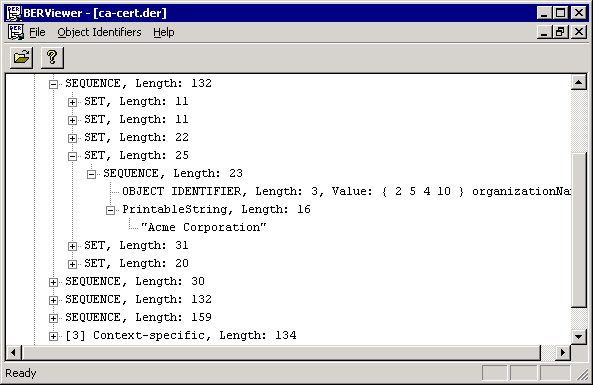
Certificate viewed using a generic BER viewer:
Critical and Non-critical extensions
If an extension is critical it can only be used for the purposes indicated.
If an extension is non-critical it is an advisory field and not restrictive.
Key Usage
The critical key usage extension controls how the public key can be used.
RFC 2459 Internet X.509 Public Key Infrastructure Certificate and CRL Profile describe the role of the different key usage extensions bits.
CRL Sign is enabled when the public key is used for verifying a signature on a CRL. Enable for CA certificates.
...
Non Repudiation is enabled when the public key is used to verify digital signatures. Enable for S/MIME signing certificates and object-signing certificates.
2.5.4 | Object Identifiers for X.500 attributes type |
2.5.4.3 | Common Name |
2.5.4.5 | Serial Number |
2.5.4.6 | Country Name |
2.5.4.7 | Locality |
2.5.4.8 | State |
2.5.4.10 | Organization |
2.5.4.11 | Organizational Unit |
2.5.29 | Object Identifiers for Version 3 extensions |
2.5.29.14 | Subject Key Identifier |
2.5.29.15 | Key Usage |
2.5.29.17 | Subject Altervative Name |
2.5.29.19 | Basic Constraints |
2.5.29.35 | Authority Key Identifier |