Page History
| Anchor | ||||
|---|---|---|---|---|
|
| Info |
|---|
There are multiple ways for you to create a self-signed certificate. The steps in this topic include KeyStore Explorer, a free third-party utility. This product is not supported by IDERA and is only an example. |
| Info |
|---|
IDERA Dashboard must be installed prior to performing this task. |
IDERA users in In environments that have not yet added a certificate signed by a Certification Authority (CA), IDERA users receive a warning message in their browser each time they attempt to open the SSL version of the IDERA Dashboard. Note that the default certificate provided with an IDERA product is not signed by any well-known CA and is intended only for use in testing purposes ONLY.
You can resolve this issue by adding a signed CA using the steps provided in Run IDERA Dashboard over SSL TLS (HTTPS), or you can use the following steps to resolve this issue at no certificate cost.
To resolve the certificate message at no cost
Adding a self-signed certificate
Create a self-signed certificate
- Launch Windows Powershell as administrator.
Create your certificate by running the following command. Leave Windows PowerShell open.
Code Block language powershell $certName = "{certificateName}" ## Replace {certificateName}Tip Replace
{certificateName}with the name that you will use to access the IDERA Dashboard. For example, if you are using thehttps://ComputerName:9291link to access IDERA Dashboard, then useComputerName. In case, you are using thehttps://ComputerName.Domain.com:9291address then useComputername.Domain.com. In this example we are usinglocalhost.Run the following command to configure your certificate settings.
Code Block language powershell $Params = @{ "DnsName" = @($certName,"{certificateName}") ## If you want to include other addresses or servers, you must separate each with a comma "CertStoreLocation" = "Cert:LocalMachine\My" "KeyExportPolicy" = "Exportable" "KeySpec" = "Signature" "KeyUsage" = @("KeyEncipherment","DigitalSignature") "KeyAlgorithm" = "RSA" "KeyLength" = "2048" "HashAlgorithm" = "SHA256" "NotAfter" = (Get-Date).AddYears(10) } ## Checks for asterisks in the $certName and replaces it with the underscore character If ($certName.Contains("*")) { $certName = $certName -replace '\*','_' }Note Replace
{certificateName}with the certificate name you previously defined in Step 2.Tip Change the
NotAfterparameter value to make your certificate valid for a more extended period.Run the command below to create your certificate defined with the parameters above.
Code Block $cert = New-SelfSignedCertificate @Params
| Anchor | ||||
|---|---|---|---|---|
|
Once the certificate is created, you need to export the certificate's private key. To do so, follow the steps below:
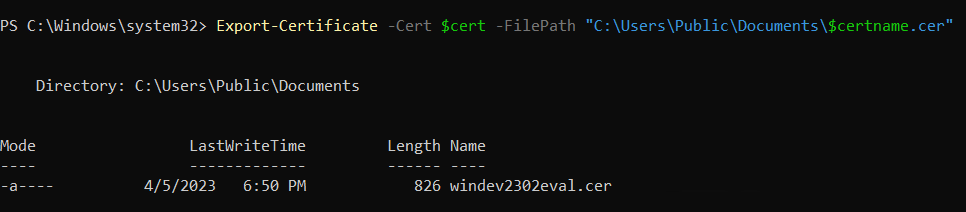
Export your certificate in
.cerformat by running the following command.Code Block language powershell Export-Certificate -Cert $cert -FilePath "{DesiredPath}\$certname.cer" ## Replace {DesiredPath} with the desired location e.g. C:\Users\Public\DocumentsOnce the certificate is created, you should be able to check the certificate specifications.
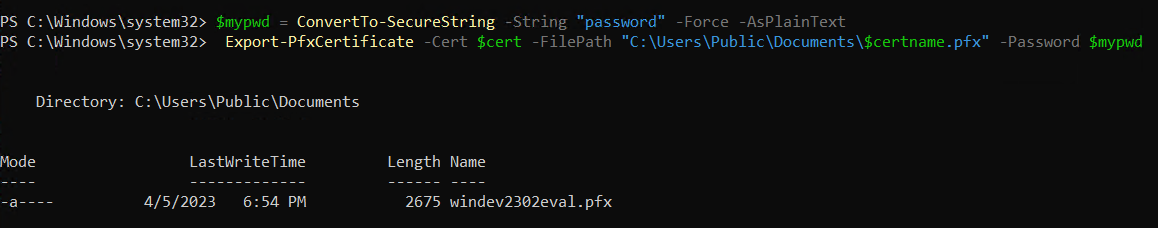
Create a password for your certificate private key and save it in a variable. Replace
{myPassword}with the password that you wish to use to protect your certificate's private key.Code Block language powershell $mypwd = ConvertTo-SecureString -String "{myPassword}" -Force -AsPlainText ## Replace {myPassword}Run the next command to export your private key, use the password you store in the
$mypwdvariable.Code Block language powershell Export-PfxCertificate -Cert $cert -FilePath "{DesiredPath}\$certname.pfx" -Password $mypwd ## Replace {DesiredPath} with your desired location e.g. C:\Users\Public\DocumentsWhen the private key is exported in a
.pfxfile, you should be able to check the certificate specifications.
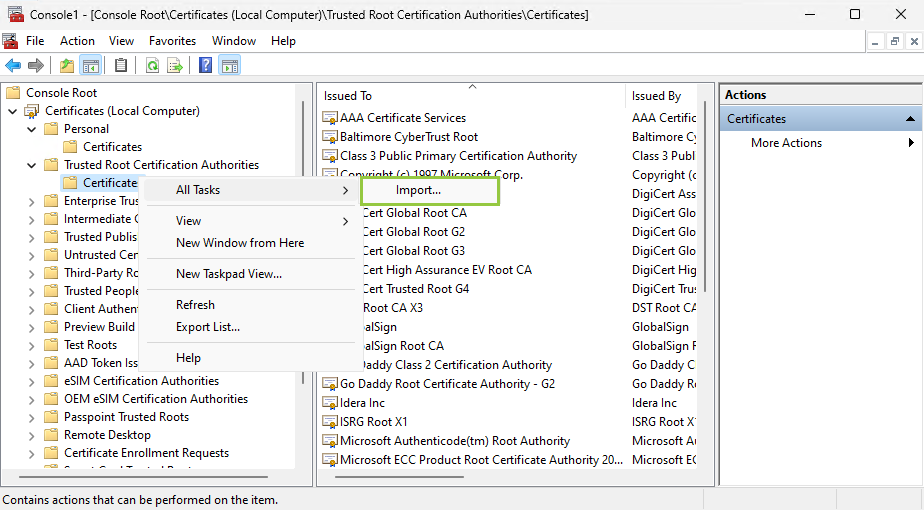
Import your private key into the Trusted Root Certification Authorities
Complete your certificate configuration by adding the .cer file to the Trusted Root Certification Authorities folder in the Console Root. To do so, follow the steps below:
- Open the Microsoft Management Console (MMC) by selecting Start > Run and typing mmc. Click OK.
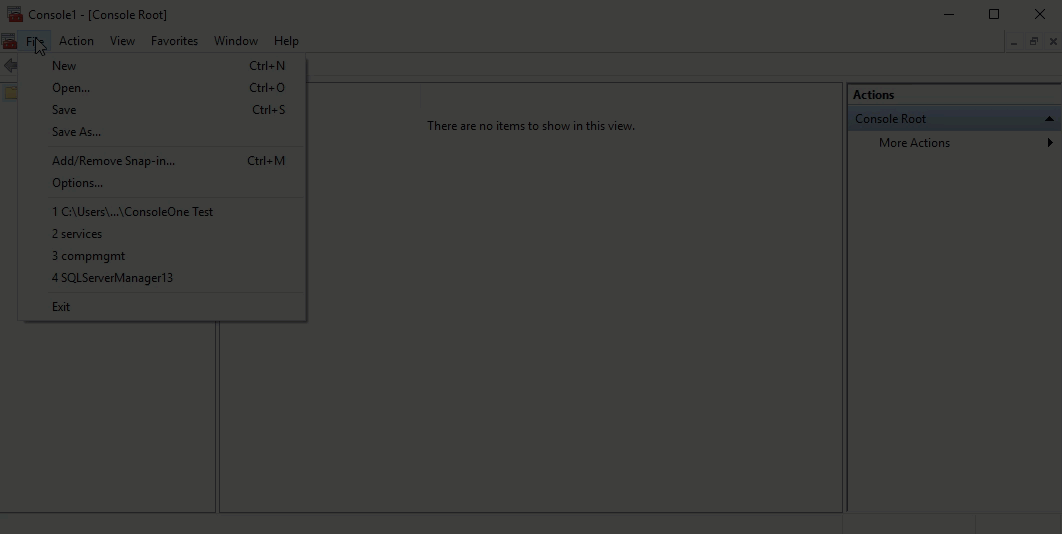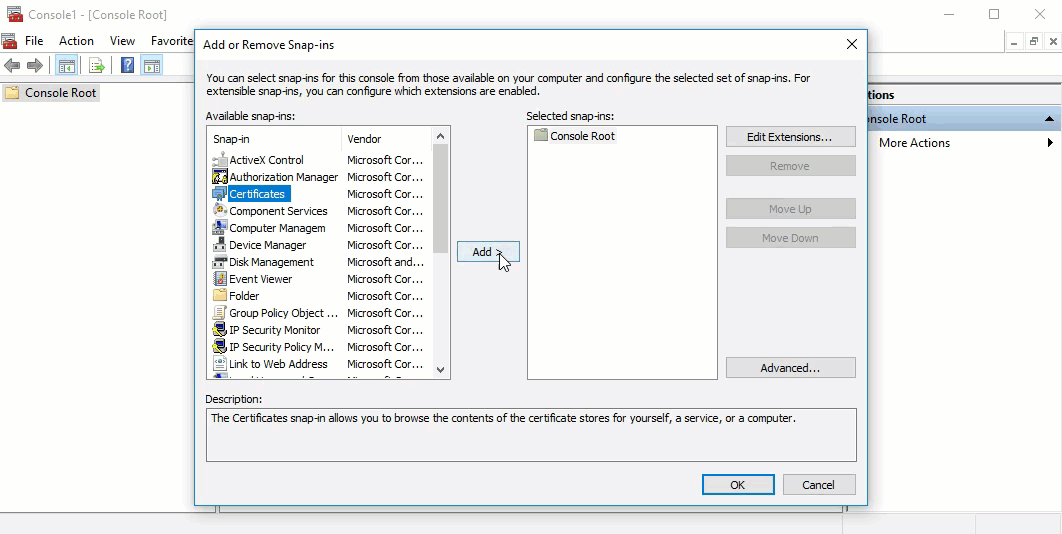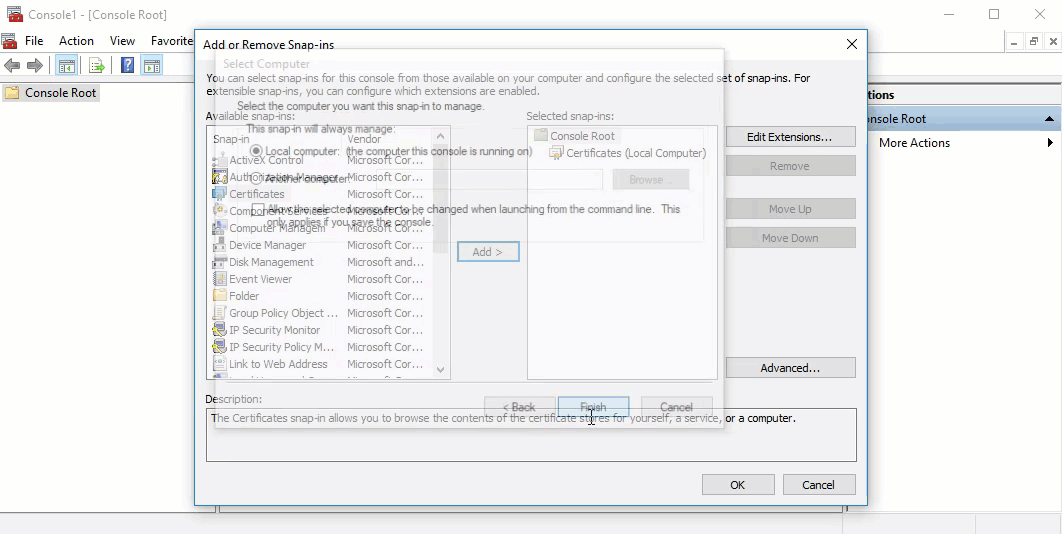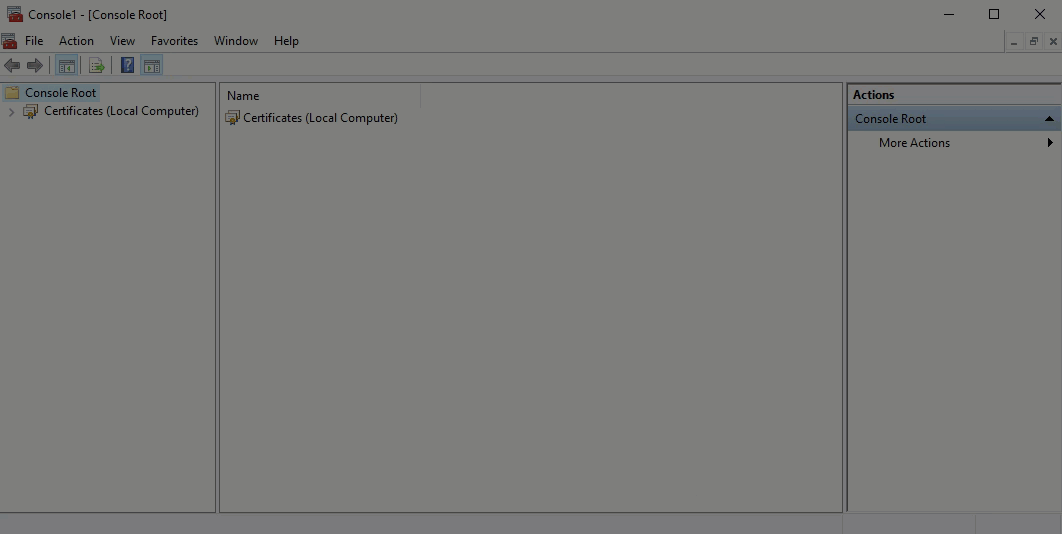
- When the MCC window opens, click File from the menu toolbar, and select Add/Remove Snap-in...
- Select Certificates from the Available snap-ins options and click Add >.
- In the Certificates snap-in window, select Computer Account, and click Next.
- In the Select Computer window, verify that Local computer is set as the computer you want the snap-in to manage. Click Finish.
- Import your certificate (
.cerfile) into the Trusted Root Certification Authorities folder. To do so, expand Certificates and right-click the Trusted Root Certification Authorities folder. Click All Tasks > Import...
Follow the Certificate Import Wizard instructions to import the
.cerfile previously created.Info When adding your certificate or private key using the Certificate Import Wizard, use the password you previously defined in the Export your certificate private key section.
Import Key Pair
- Download the free KeyStore Explorer utility from
and install it.Newtab2 alias http://keystore-explorer.org/ url http://keystore-explorer.org/ - Open KeyStore Explorer as administrator. On launch, it may ask you to download an updated Java Cryptography Extension (JCE) Unlimited Strength file.
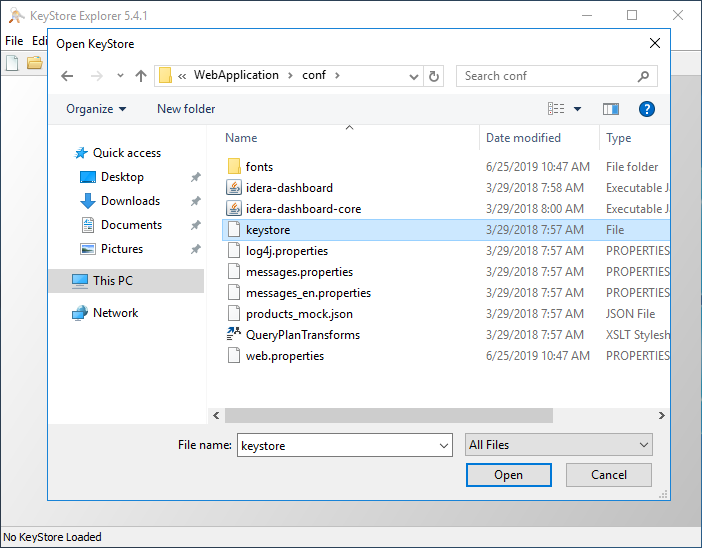
- Click Open an existing KeyStore.
- Browse to the IDERA Dashboard conf directory (the default path is
C:\Program - Download the free KeyStore Explorer utility from the following website:
http://keystore-explorer.sourceforge.net/ - Install the utility.
- Open KeyStore Explorer. KeyStore Explorer displays the following Quick Start options. On launch, it may ask you to download an updated Java Cryptography Extension (JCE) Unlimited Strength file.
- Open the KeyStore Explorer console by clicking Open an existing KeyStore. KeyStore Explorer displays the Open KeyStore window.
- Browse to the IDERA Dashboard \conf directory (e.g. C:\Program Files\Idera\Dashboard\WebApplication\conf), and then open the keystore file.
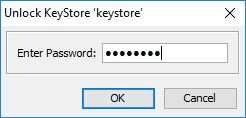
KeyStore Explorer displays the Unlock KeyStore window. - In the Enter Password field of the Unlock KeyStore window, type:
password
and then click OK.
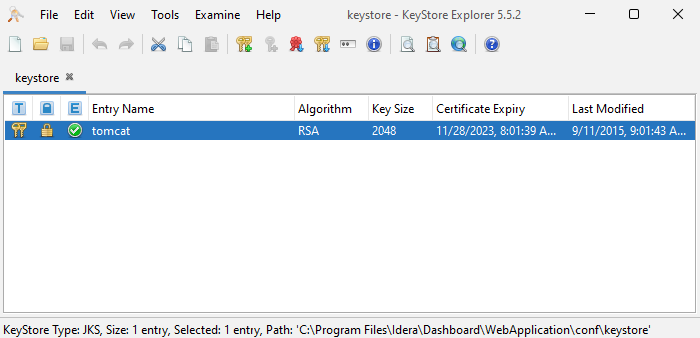
KeyStore Explorer displays a list of any existing certificates, as shown in the following image.
- Create a new key pair by selecting the existing key, and then clicking the Generate Key Pair icon, as shown in the following image.
- In the Generate Key Pair window, verify the proper algorithm is selected, and then click OK.
KeyStore Explorer begins to generate a new key pair
and then displays the Generate Key Pair Certificate window. - In the Generate New Pair Certificate window, make the following changes:
- In the Signature Algorithm list, select SHA-1 with RSA or SHA-256 with RSA. This example uses SHA-1 with RSA.
- In the Validity Period fields, select the number of years the certificate is valid. This example uses 5 years.
- Click the Edit Name icon to enter identifying information.
KeyStore Explorer displays the Name window. - In the Name window, complete each of the available fields. The entry in the Common Name (CN) field should correlate with the name of the website.
In essence, the name that you provide should match the URL that you intend to use. For example, the following image shows an entry that creates a certificate for https://localhost.
Click OK. KeyStore Explorer displays the New Key Pair Entry Alias window.
- Verify that the displayed alias matches the name of your website, and then click OK.
KeyStore Explorer displays the New Key Pair Entry Password window. - Type and confirm the password you want to use for the key pair, and then click OK. Note that this password must match the password entered in step 6.
In this case, type the following password in both input boxes:
password
KeyStore Explorer displays a message stating that the key pair generation is successful. - Click OK to close the success window, and then verify the new line in the KeyStore Explorer certificate list, as shown in the following image.
- Delete the old certificate by selecting the appropriate line, and then clicking the Cut icon, as shown in the following image.
- Click the Save icon, as shown in the following image.
- Restart the IDERA Dashboard Web Application service.
- Double-click on the certificate that you created to see the details.
- Click Export and save the certificate to conf directory in the IDERA Dashboard conf directory (e.g. C:\Program\
Files\Idera\Dashboard\WebApplication\conf\) Click OK on the certificate details window to close it.
Open Certificate Manager by pressing Win+R to summon the Run dialog box, type certmgr.msc, and press ENTER.
If you are prompted for an administrator password or confirmation, type the password or provide confirmation.
Right-click on the Trusted Root Certification Authorities > Certificate node and select All Tasks > Import.
On the Certificate Import Wizard, click Next.
Select the certificate that was exported and click Open.
Click Next.
- Select Place all certificates in the following store. The correct store would be Trusted Root Certificate Authorities. Then click next.
- Click Finish.
- Select Yes.
- Click Ok on the confirmation window.
- At this point, you will need to close any browser that is open and then attempt to access the IDERA Dashboard.
| Excerpt |
|---|
IDERA Dashboard provides an integrated user experience for the IDERA products in your environment. |
...
), and open the keystore file.- On the Unlock KeyStore dialog window, enter "password" and then click OK.
- KeyStore Explorer displays a list of any existing certificates. Delete the existing key and click the Import Key Pair button.
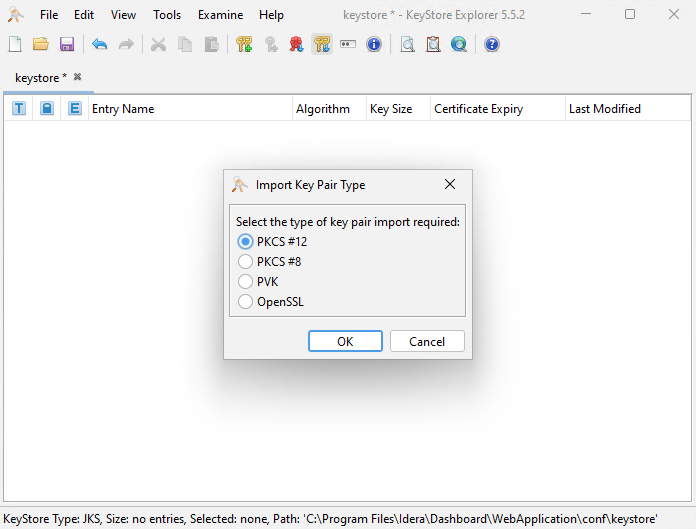
- Select PKCS #12 as the type of key you want to import, and click OK
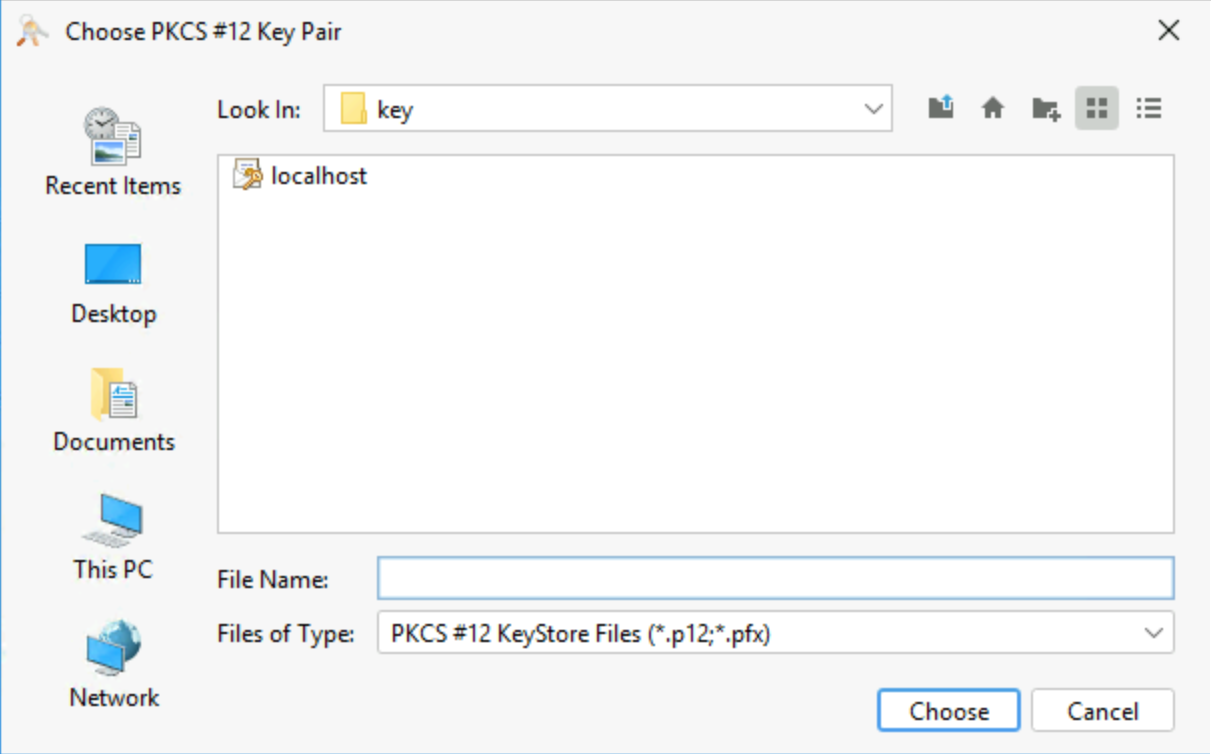
- Look for the key you created steps above (in this case,
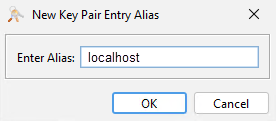
localhost.pfx) andclick Choose. - Select an alias for your key, and click OK.
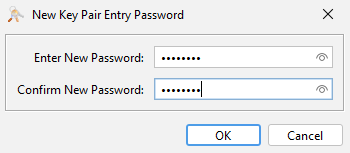
- In Enter New Password type "password", confirm, and click OK.
- When the configuration is completed the following message pops up, click OK.
- Return to the main KeyStore Explorer window, save your configuration, and close the application.
- Close all the opened browsers.
- Restart Idera Dashboard Core Service and Idera Dashboard Web Application Service.
- Access to IDERA Dashboard with the following link
https://<{certificateName}>:9291.
...